Perform a scan on Metaspoitable 2 using OpenVAS
2022-12-18
The OpenVAS vulnerability scanner presents itself as a complimentary tool conceived to enable users in promptly and effortlessly conducting precise scans of their computer systems. With a cost-free nature, daily updates, and a user-friendly interface, it emerges as the perfect selection for autonomous penetration testers or modest business system administrators in search of an economical and instinctive avenue for pinpointing plausible security vulnerabilities. In cases of more extensive enterprises, Greenbone (the entity steering OpenVAS) provides a premium edition, furnishing supplementary enterprise-oriented vulnerability scanning alternatives, thereby delivering a holistic and comprehensive solution for vulnerability assessment.
Now that we have Openvas installed and configured, its time to perform some scan on the machines we have in the LAN
Step 1
Start the openvas application
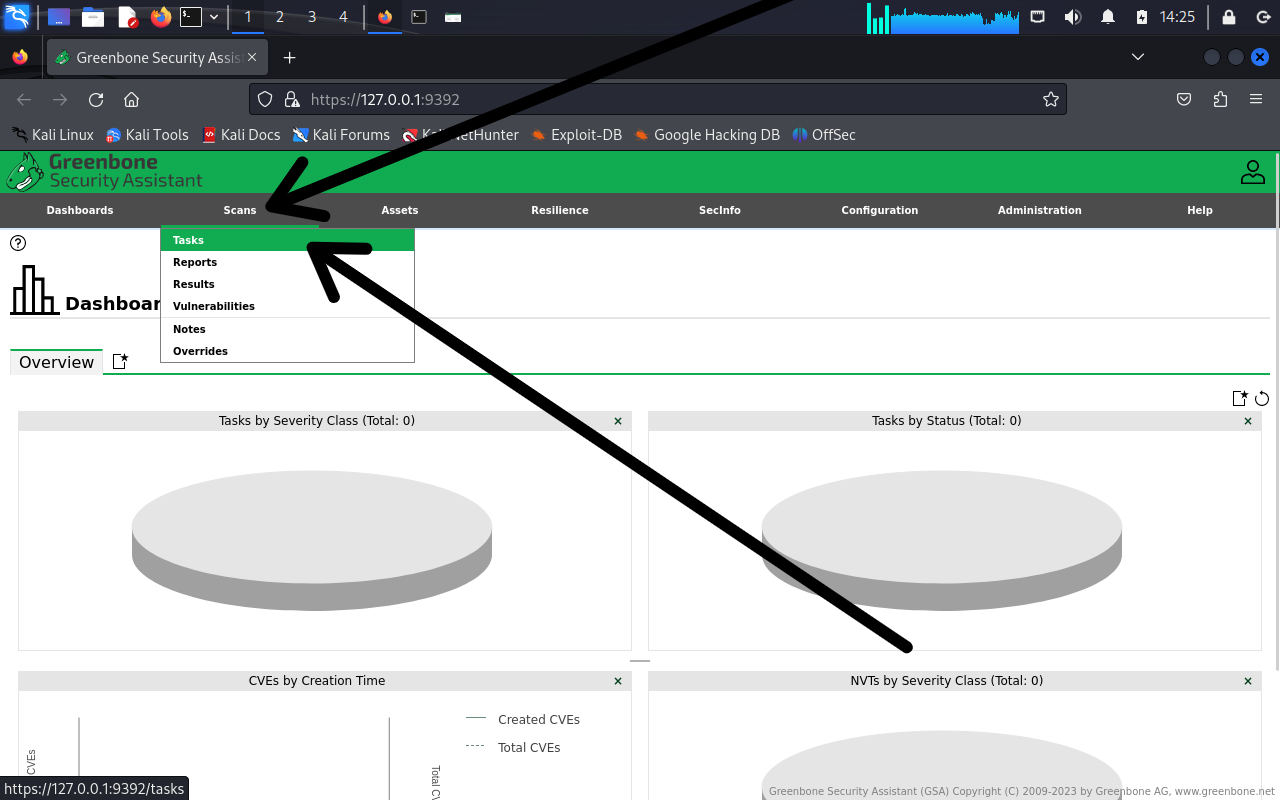
Click on "Scans" and then select "Tasks"
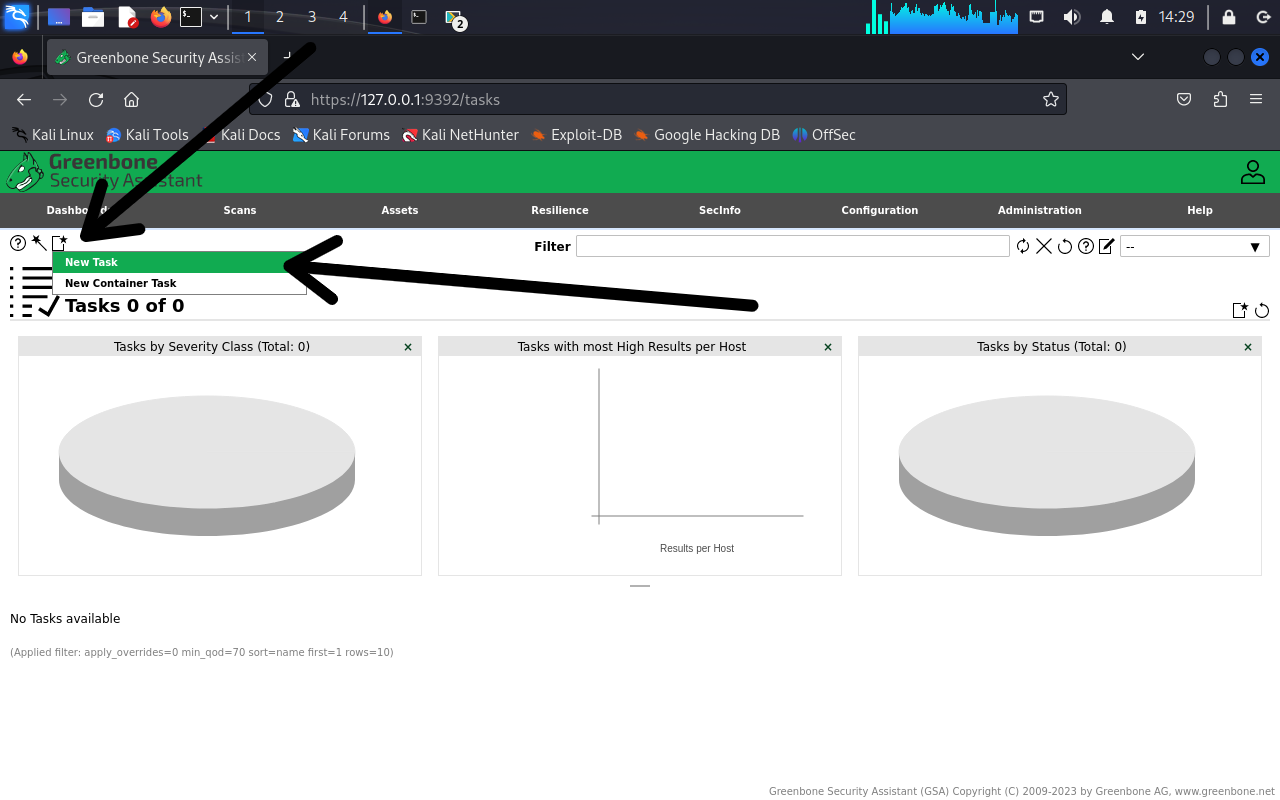
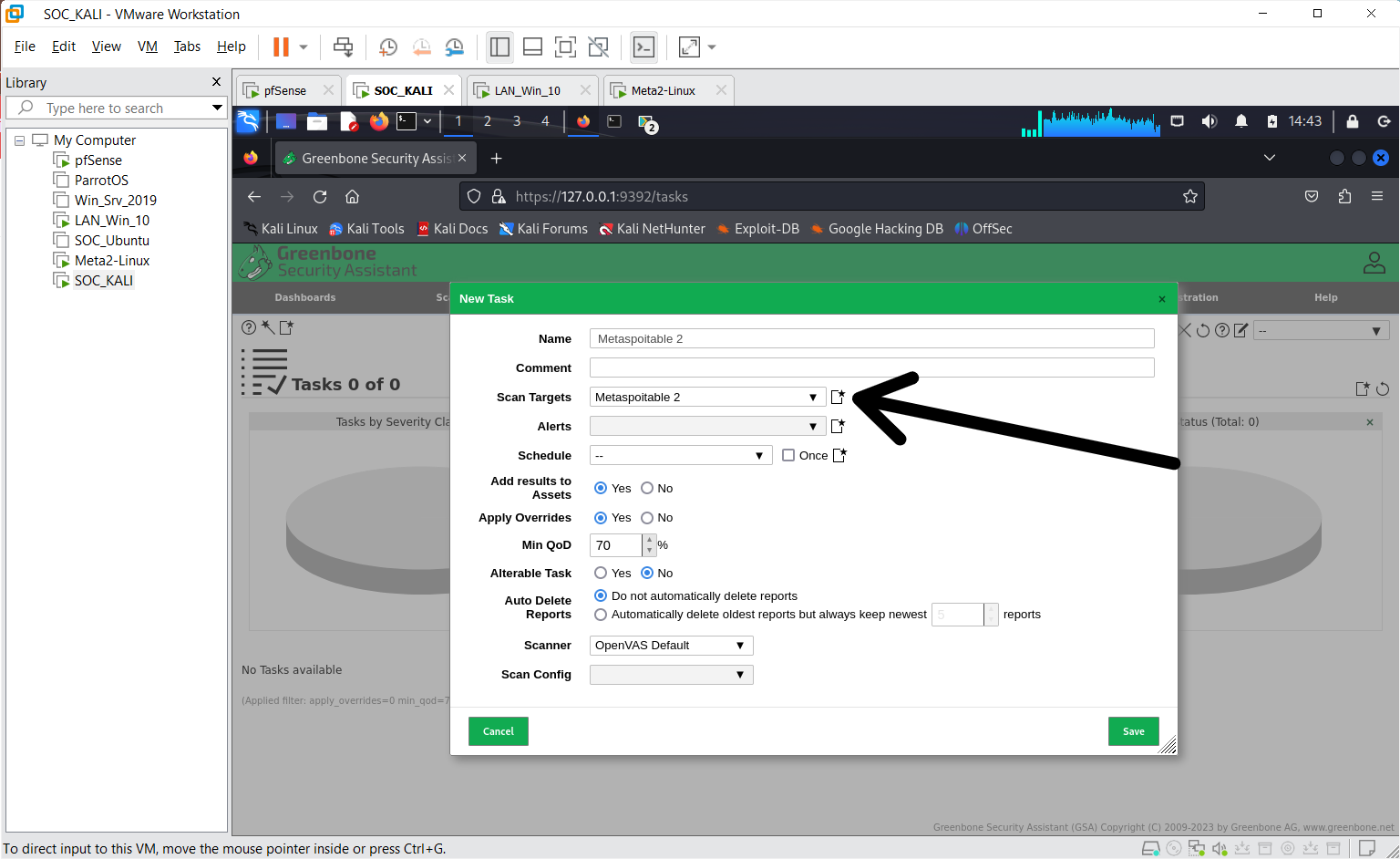
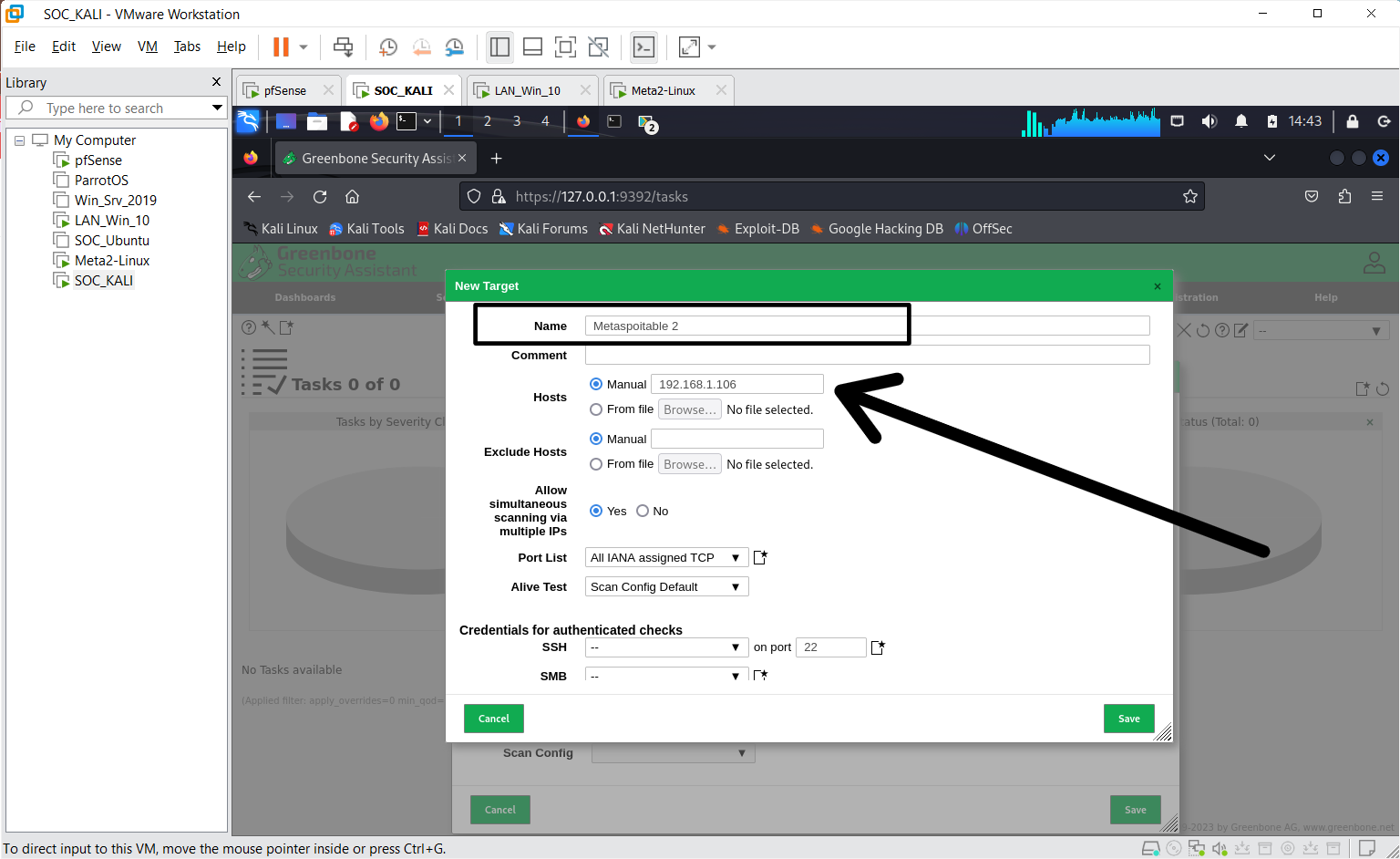
Step 2
failed to find config 'daba56c8-73ec-11df-a475-002264764cea'
Run into a configuration issue
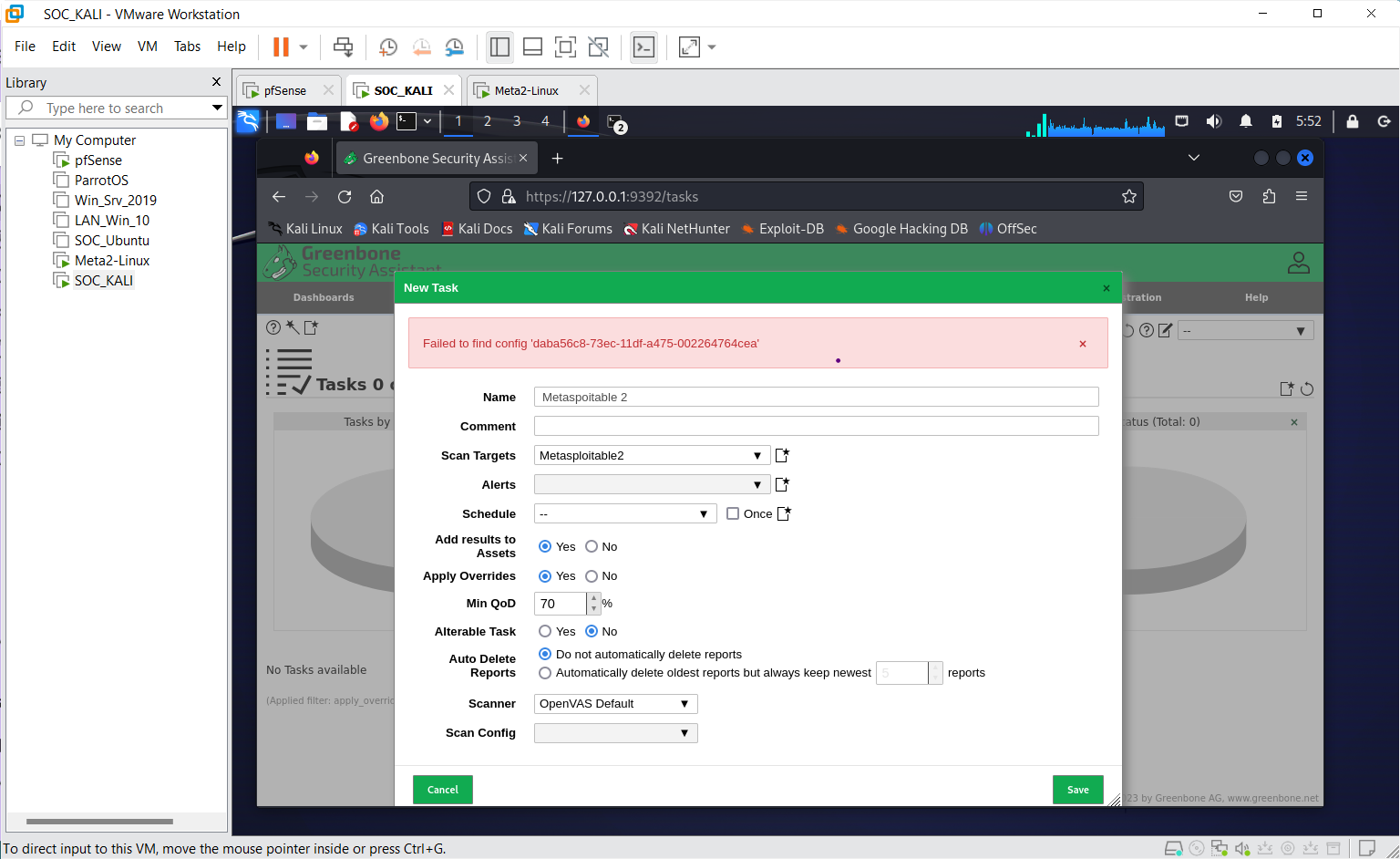
The work around this is to cancel the task and head back to the dashboard
On the"Administration " tag, select "Feed status"
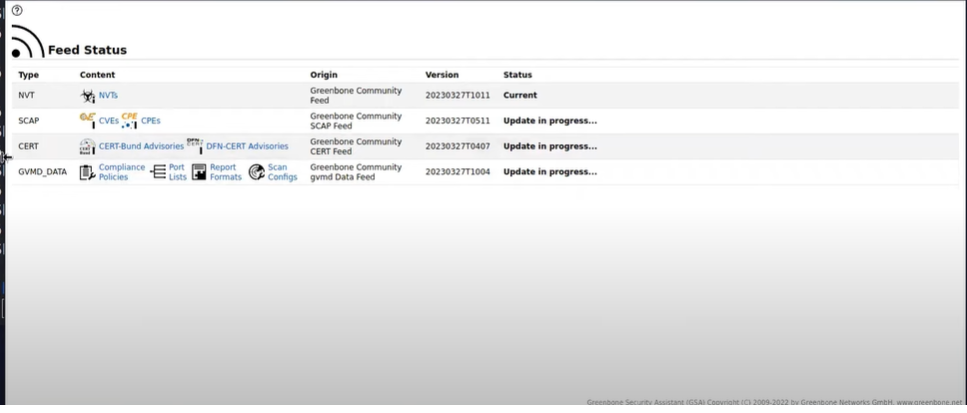
The error above occurs because the feed is not updated. Just wait for it to finish and try again
Step 3
Start the scan by clicking on the start button
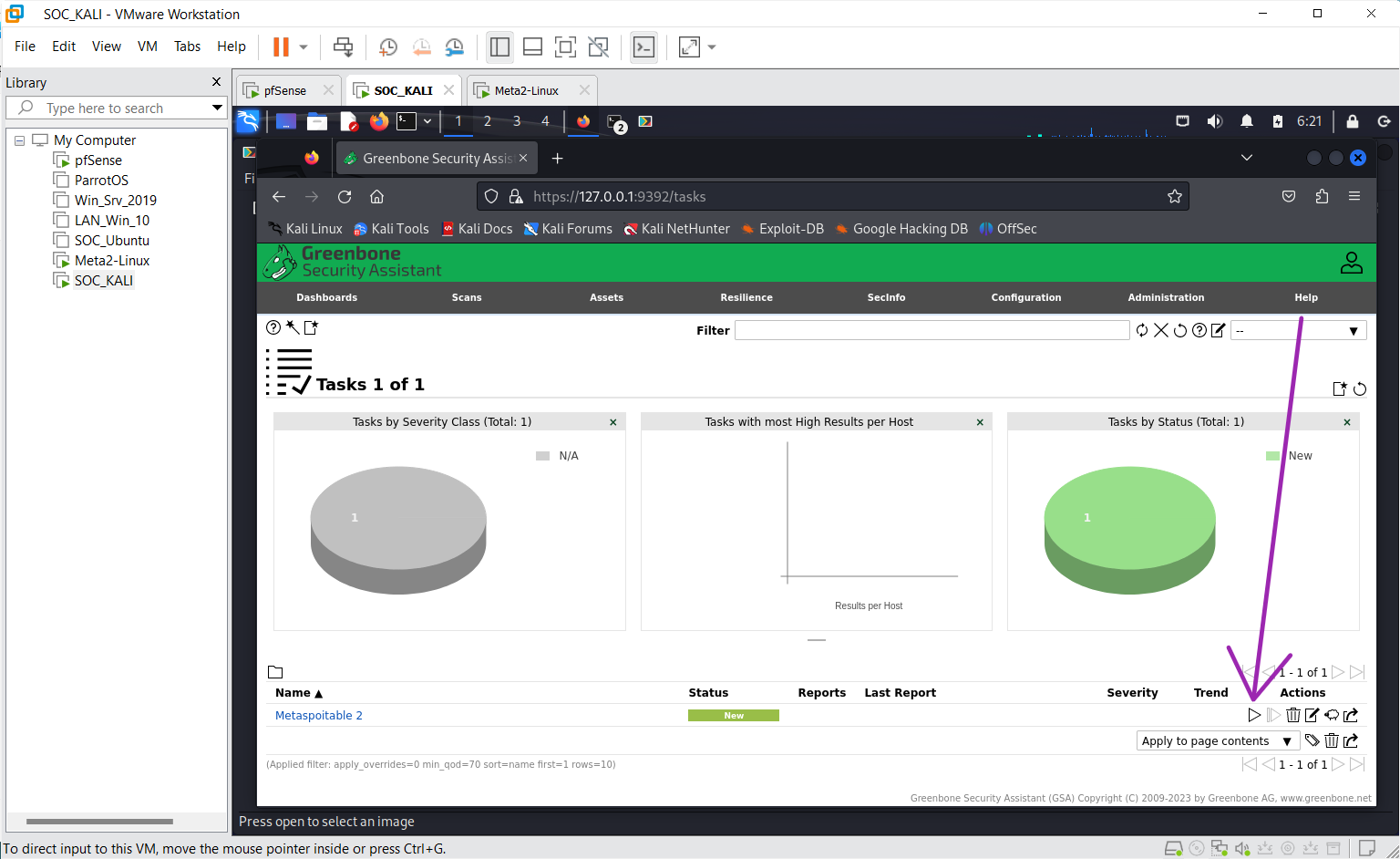
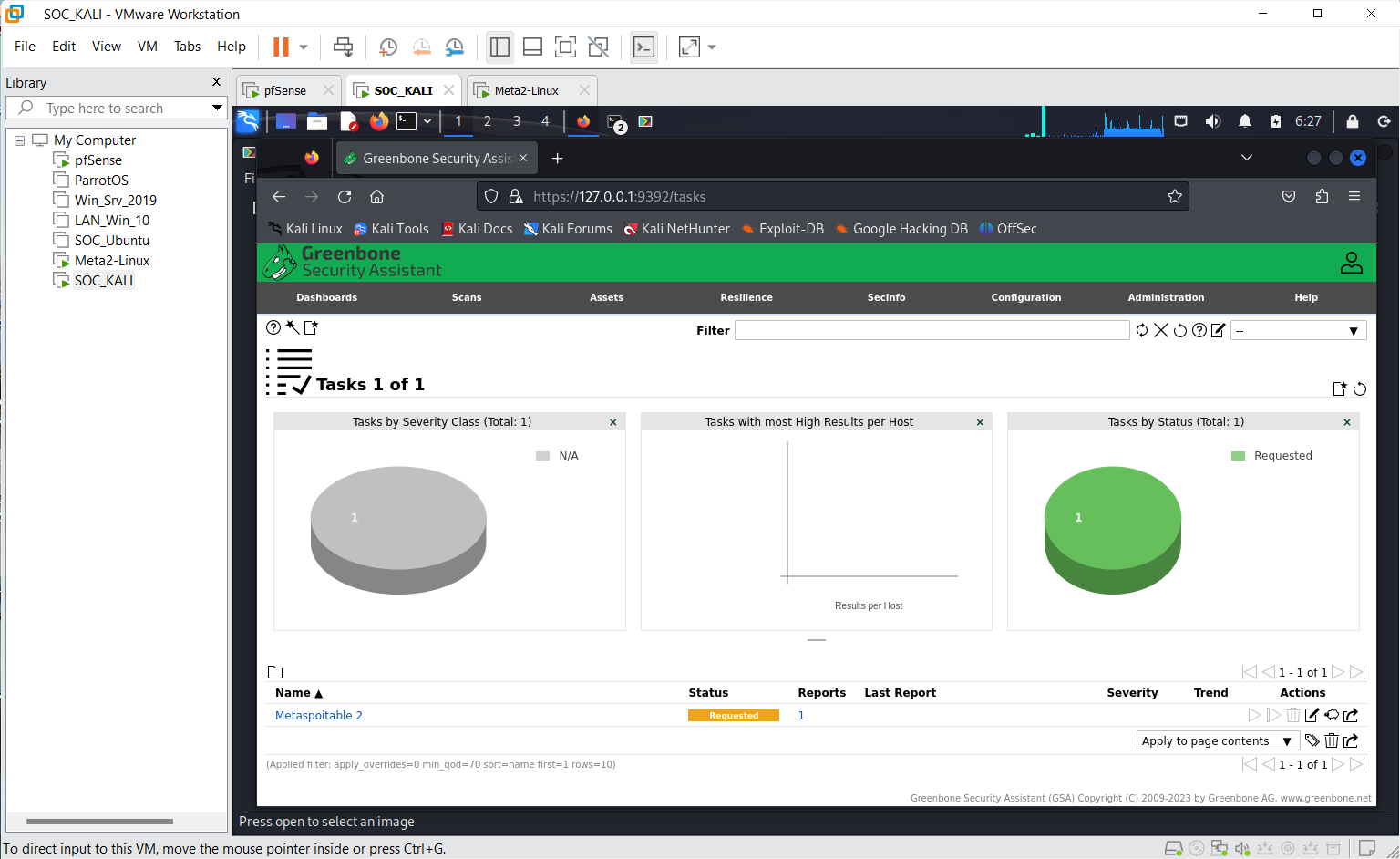
NB: The scan can take a bit of time based on intensity or amount of target so give it time
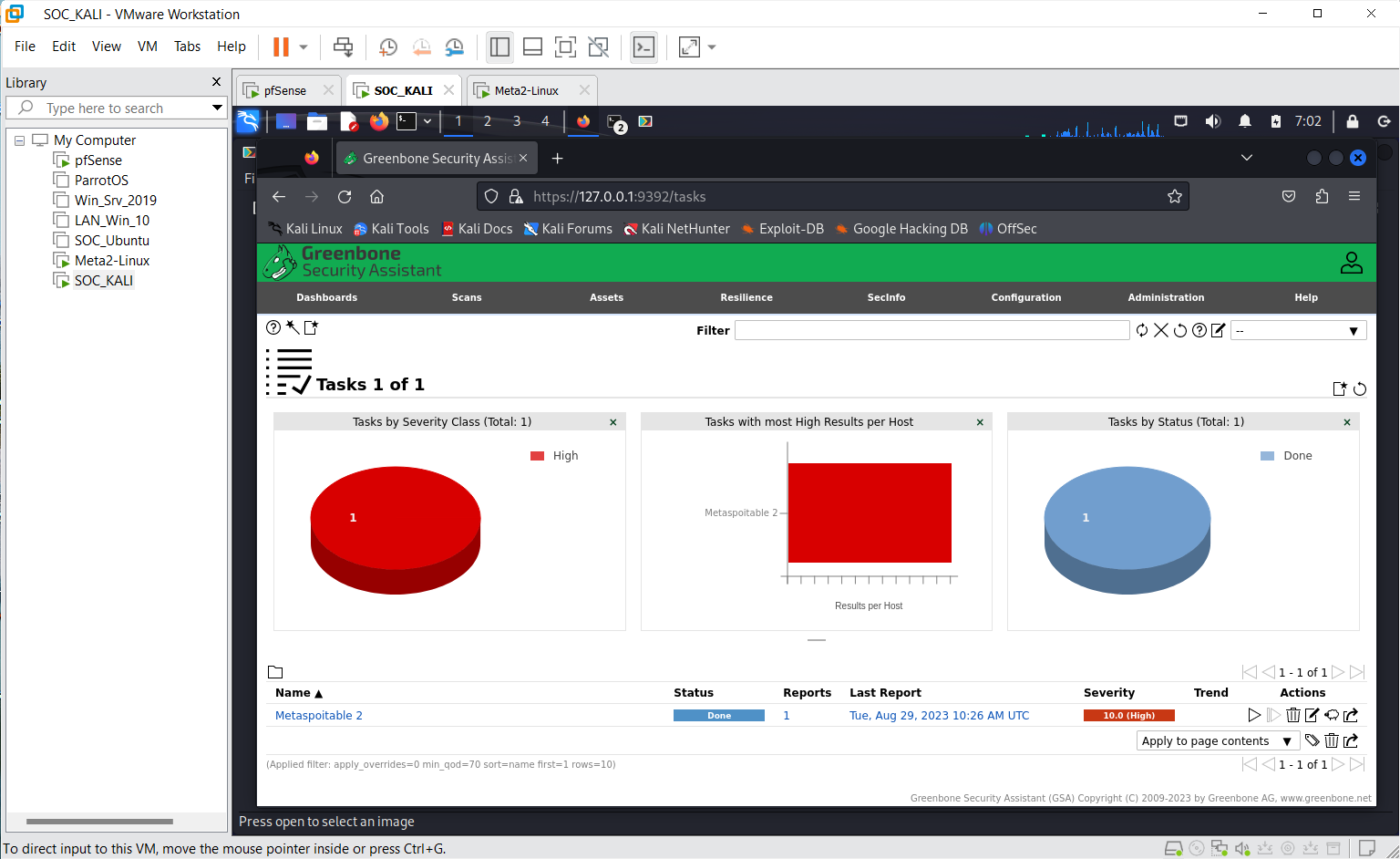
Step 4
As already expected, the target is known to be vulnerable, the scan shows a very high severity (7.0 - 10.0)
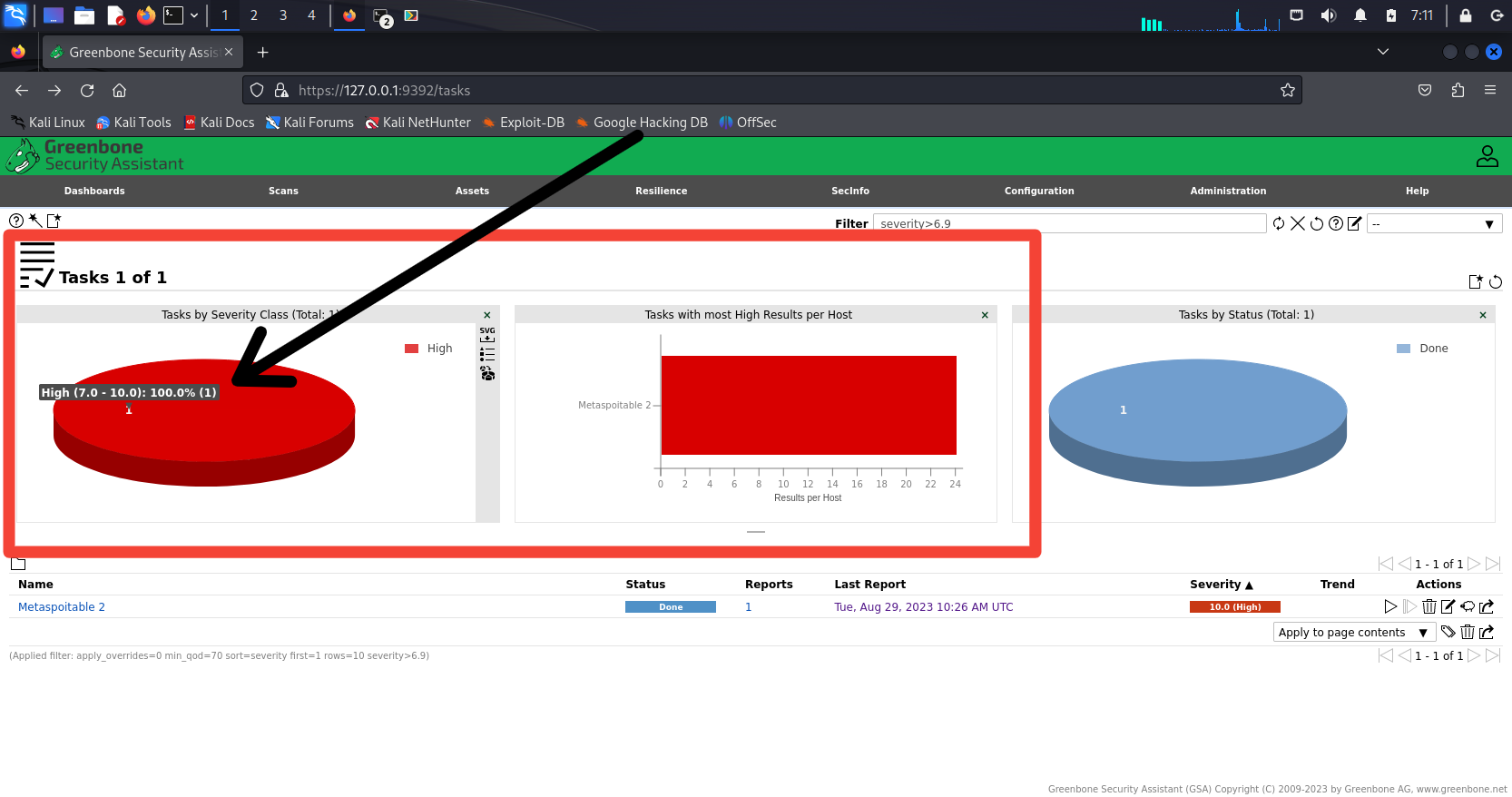
Next, click on the report to get a detailed view of the results
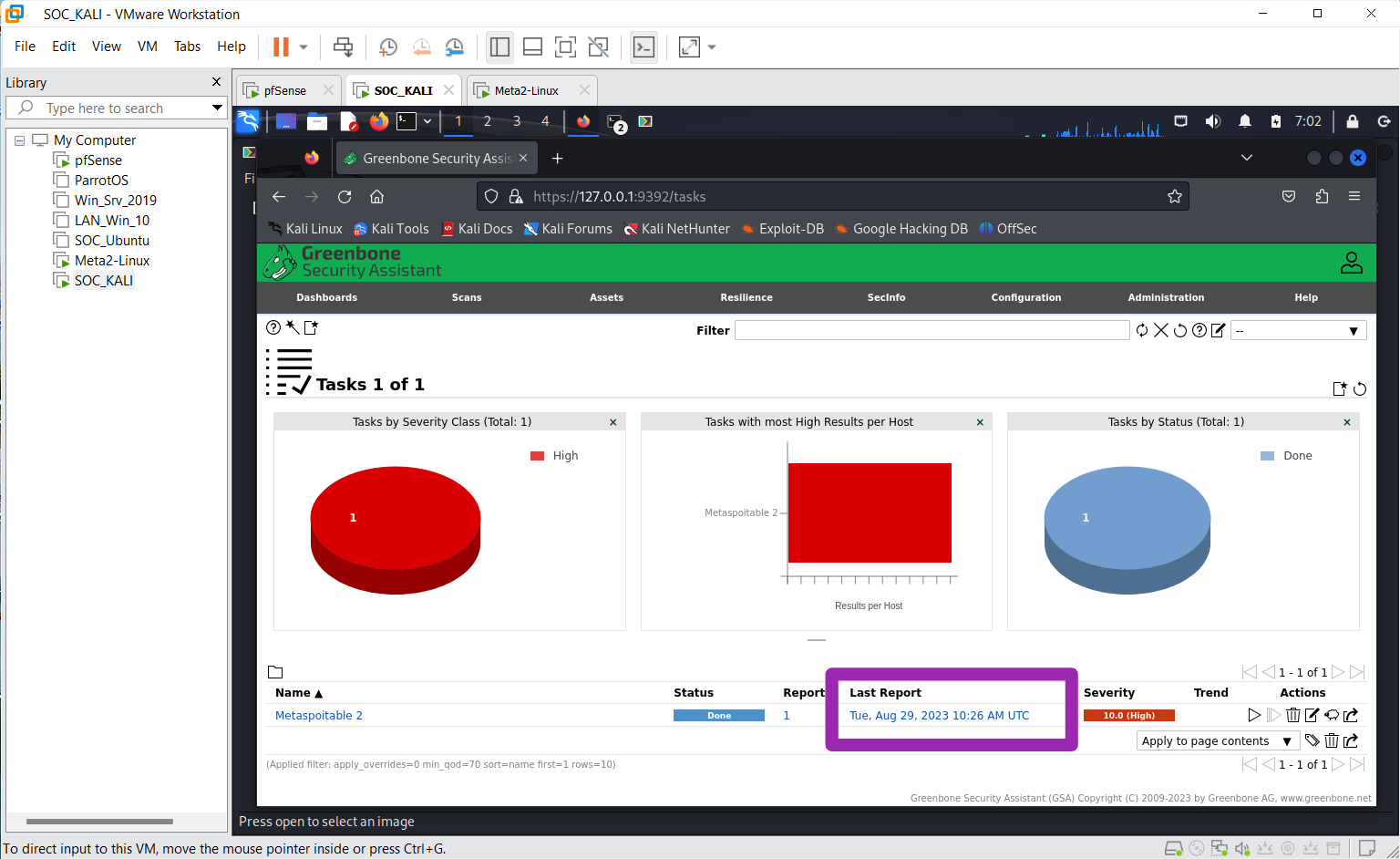
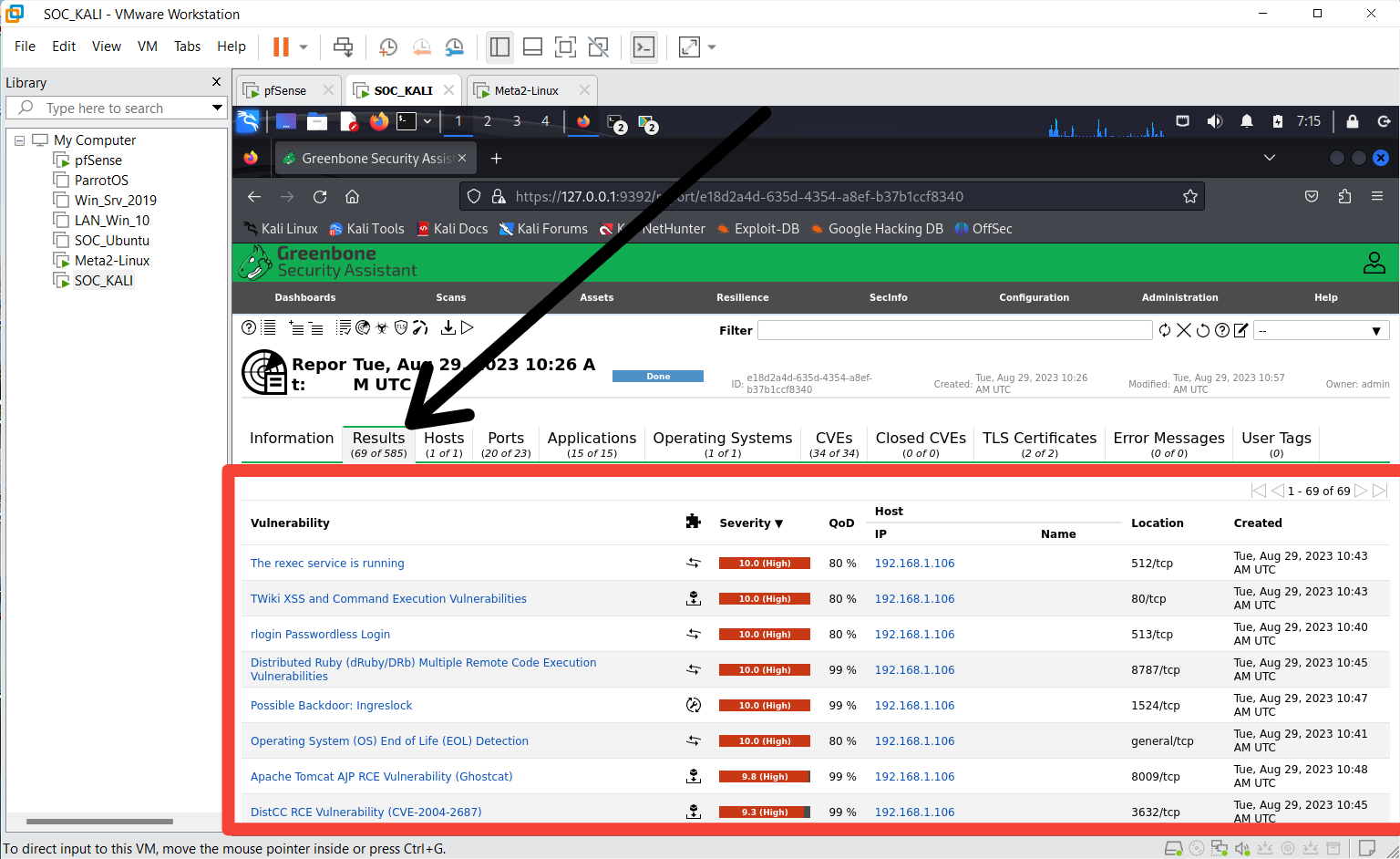
Step 5
Diving deep into the first listed vulnerability. Openvas does a good job by explaining the kind of vulnerability and how to mitigate it.
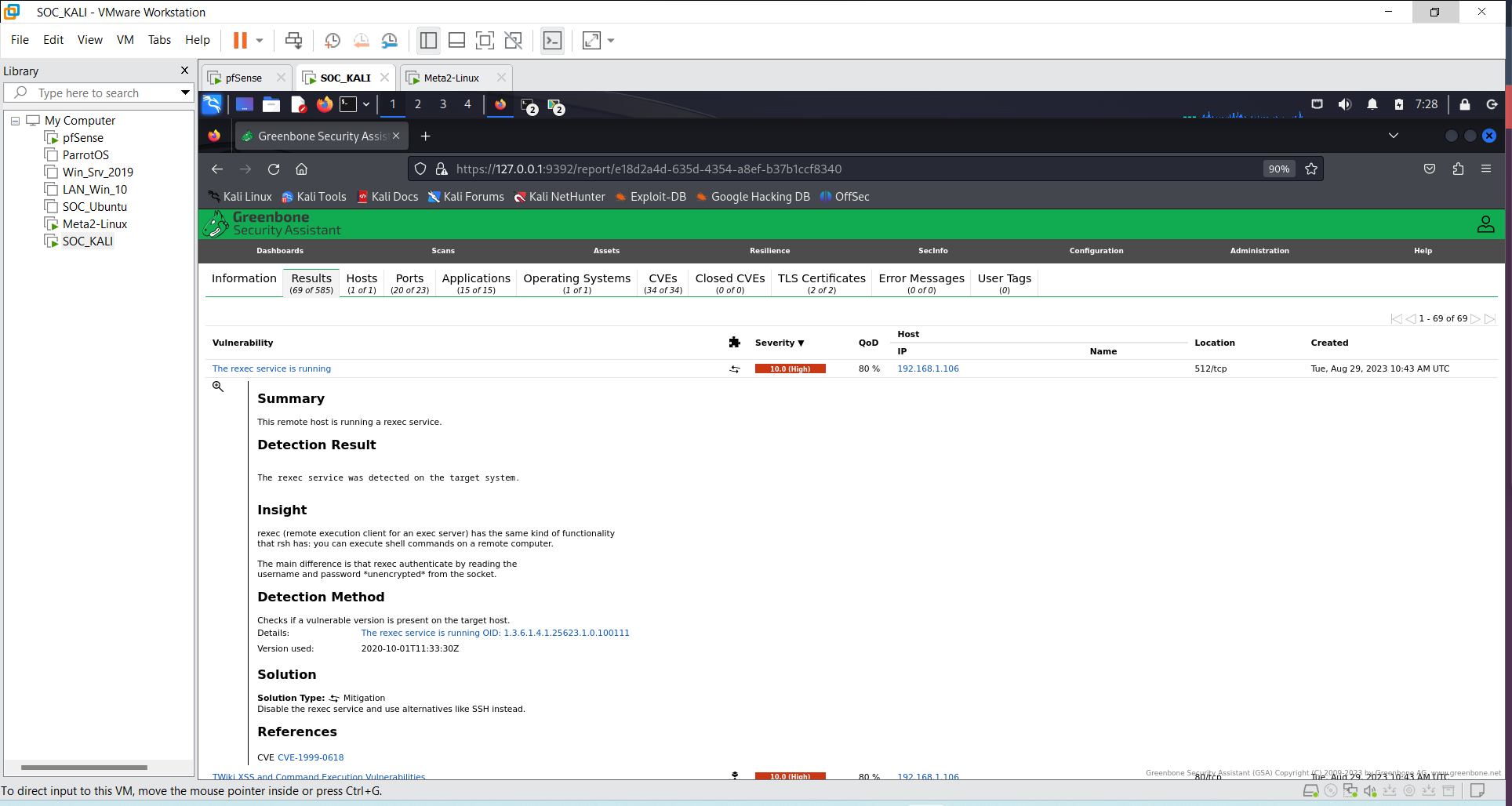
Summary
This remote host is running a rexec service.
Detection Result
The rexec service was detected on the target system.
Insight
rexec (remote execution client for an exec server) has the same kind of functionality that rsh has: you can execute shell commands on a remote computer.
The main difference is that rexec authenticate by reading the username and password *unencrypted* from the socket.
Detection Method
Checks if a vulnerable version is present on the target host.
Details:
The rexec service is running OID: 1.3.6.1.4.1.25623.1.0.100111
Version used: 2020-10-01T11:33:30Z
Solution
Solution Type: Mitigation
Disable the rexec service and use alternatives like SSH instead.
References
CVE : CVE-1999-0618
