Make Active Directory Vulnerable - Windows Server 2019
2022-11-05
NB: This post is part of the series on building a home lab
Vulnerable AD Configuration:
Create a vulnerable Active Directory that allows one to test most of Active Directory attacks in home lab.
Supported Attacks Are Abusing ACLs/ACEs, Kerberoasting, AS-REP Roasting, Abuse DnsAdmins, Password in Object Description, User Objects with Default password, Password Spraying, DCSync, Silver Ticket, Golden Ticket, Pass-the-Hash, Pass-the-Ticket and SMB Signing Disabled.
credits to the owner of this repo on github
Step 1
Run the following code in the powershell console
# if you already installed Active Directory, just run the script !
IEX((new-object net.webclient).downloadstring("https://raw.githubusercontent.com/wazehell/vulnerable-AD/master/vulnad.ps1"));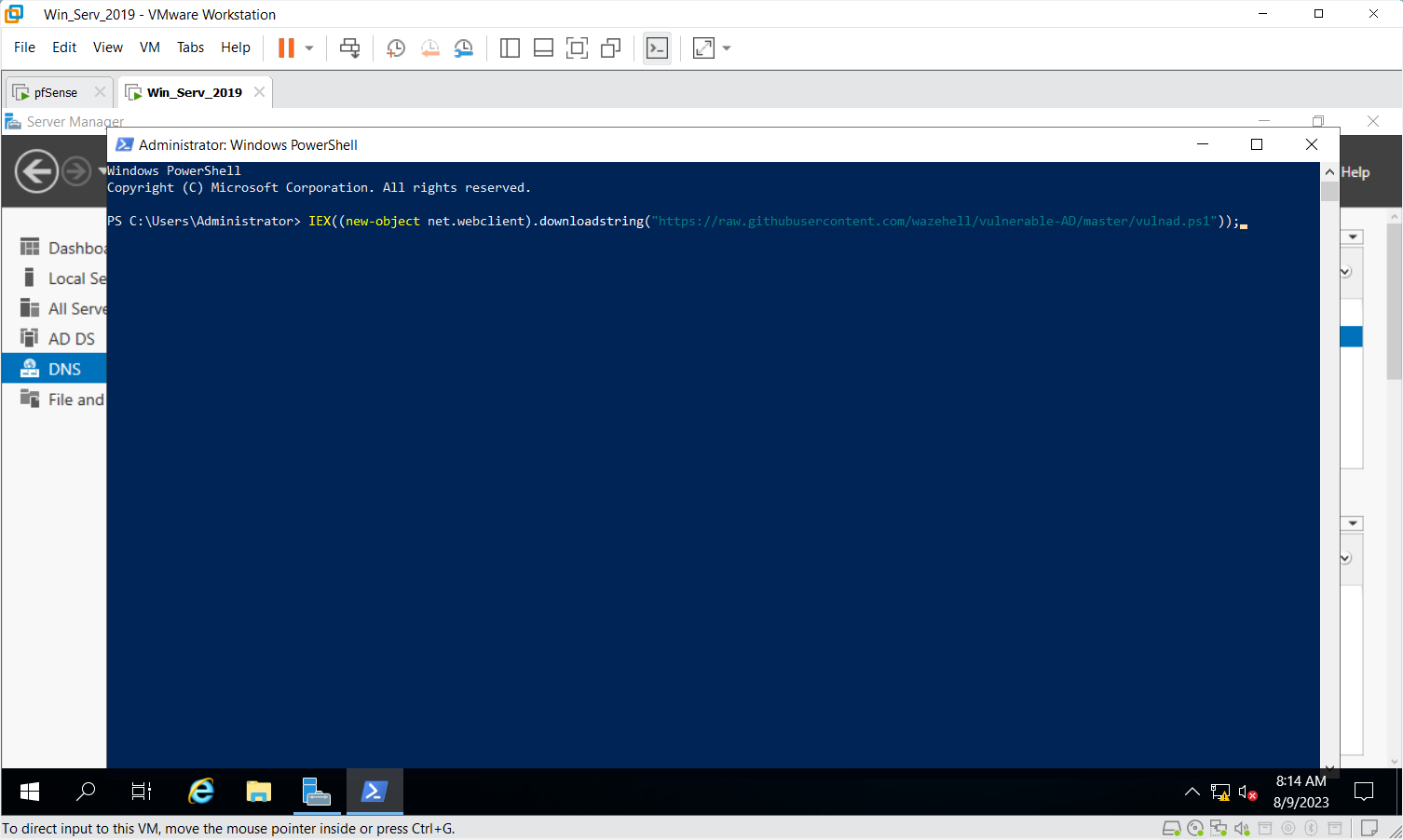
Replace the DomainName with yours mine is "ad.local"
Invoke-VulnAD -UsersLimit 100 -DomainName "ad.local"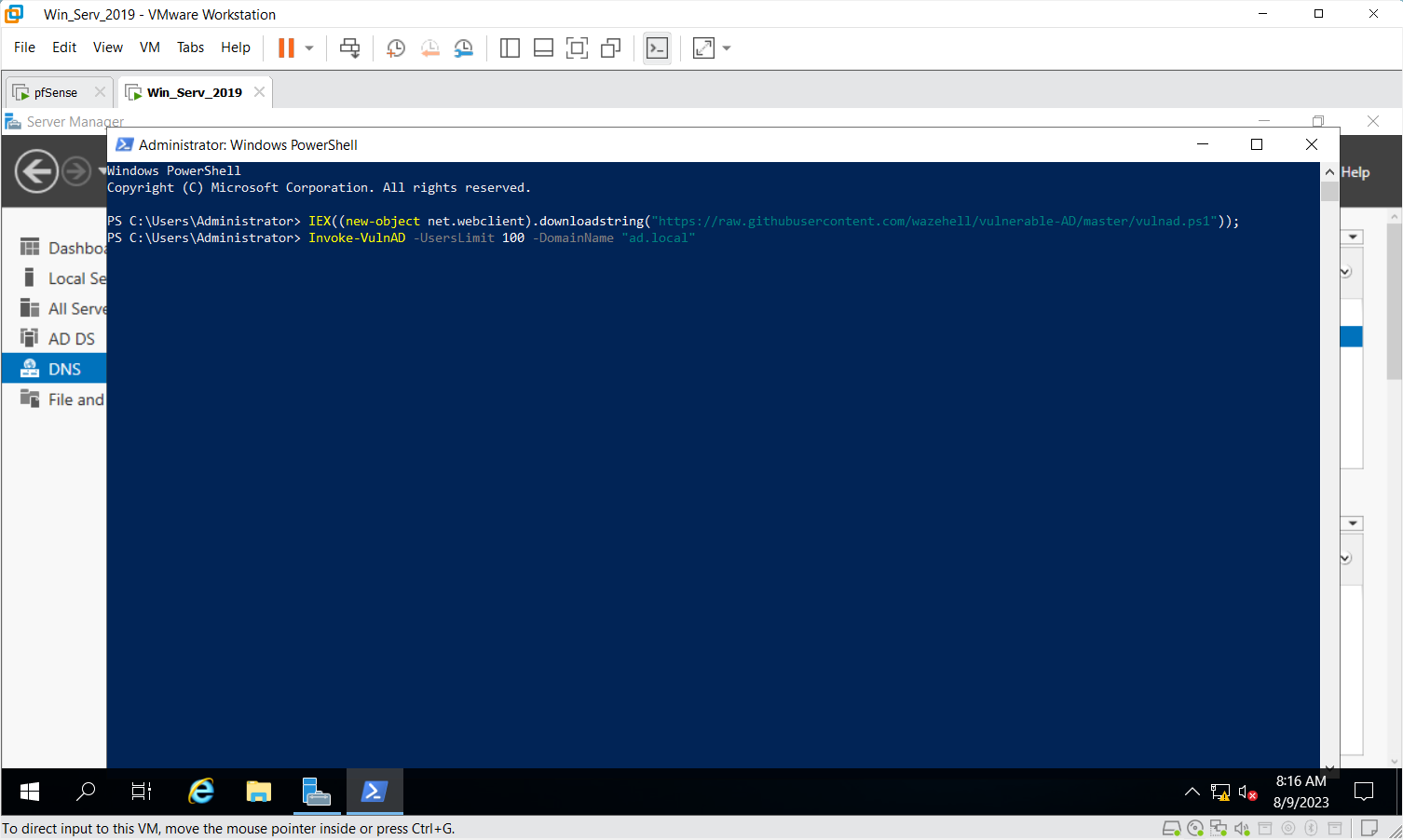
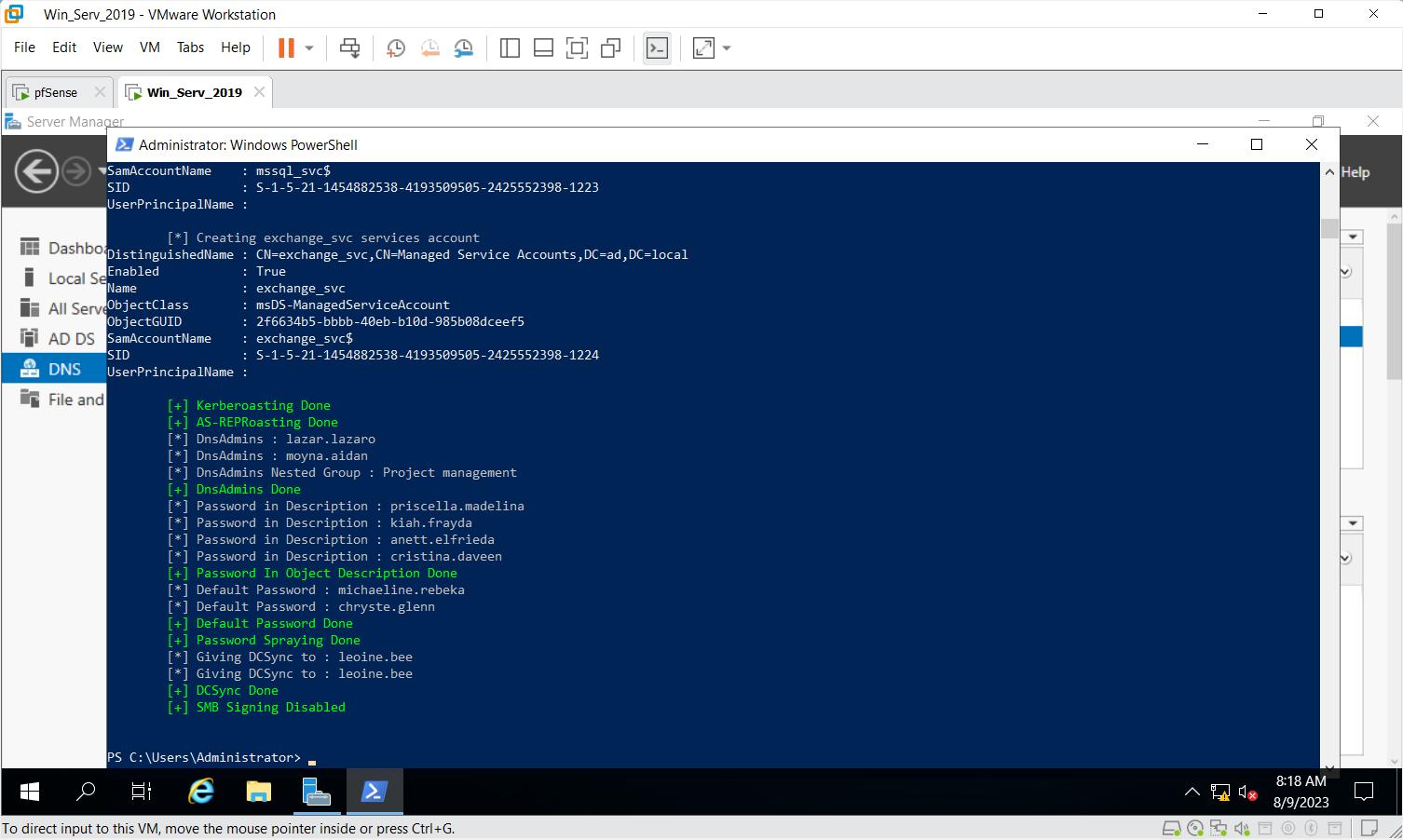
Step 3
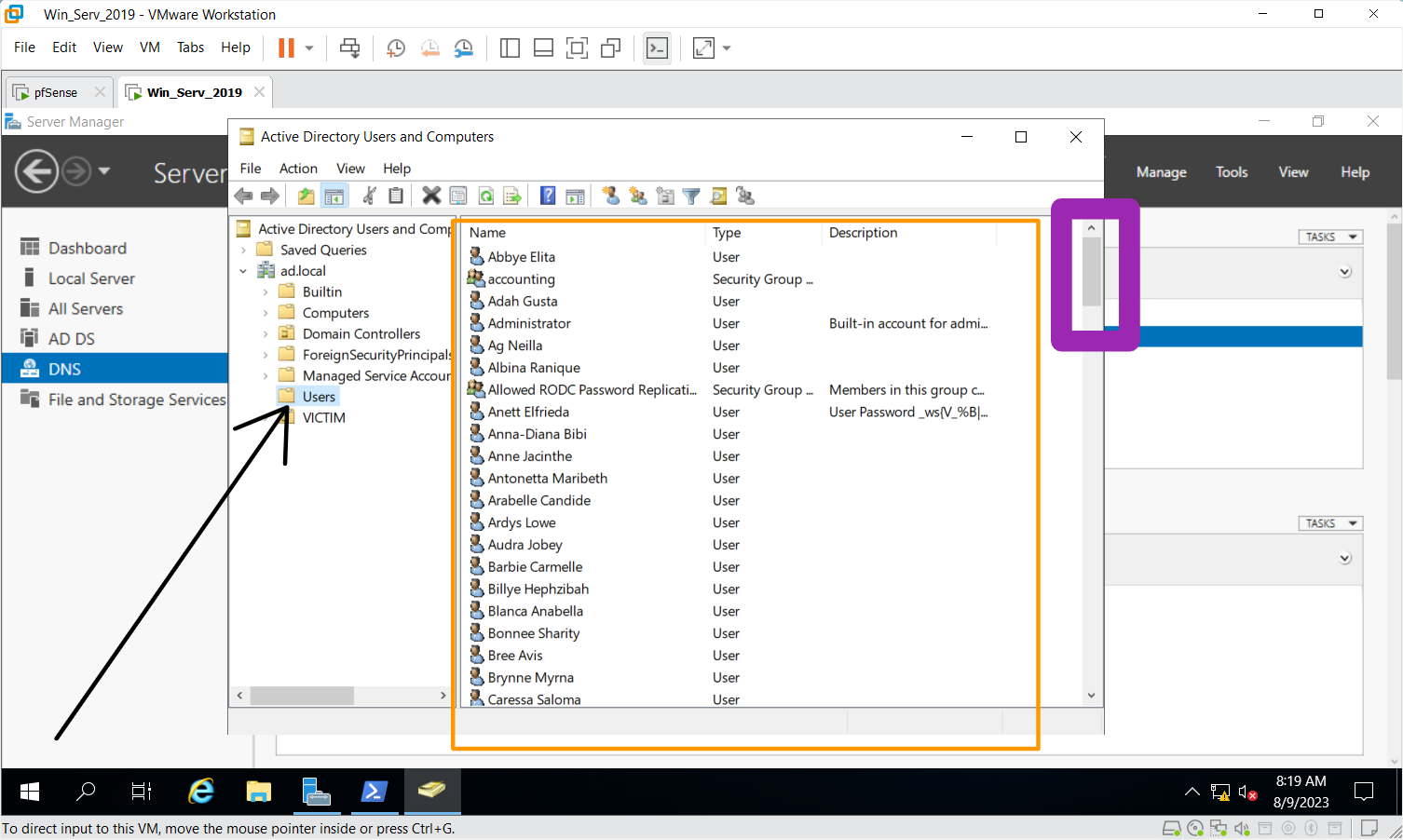
Check if the users have been created using the scripts
That's all for now. The AD is vulnerable to all kinds of attacks
Next in the homelab series : Join the Windows 10 PC to the AD Domain
